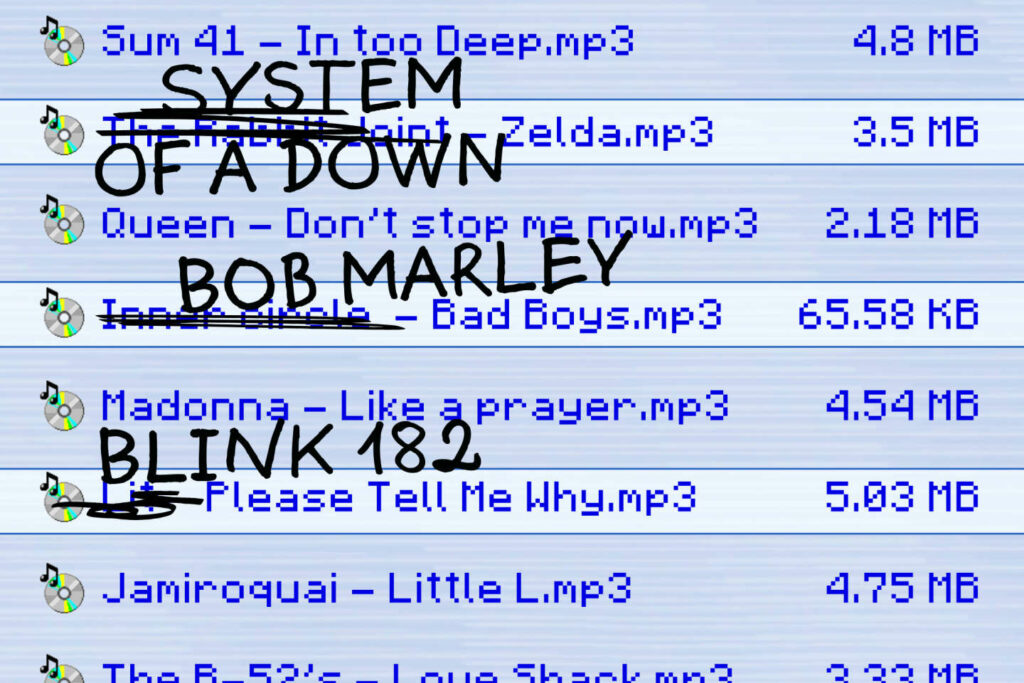
In the early 2000s, as the Internet began to sprout in homes, an incongruous track from System of a Down played on CD players on a loop: titled The Legend of Zelda, we can hear the singer of the American group, Serj Tankian, sing in his characteristic voice an ode in honor of Link, the knight of the Nintendo saga. All accompanied by basic instrumentation and cries of joy suggesting that the piece was recorded on a whim, during a public performance.
Except that this recording of the group has, in reality, never existed. Going against what many persist in believing even today, System of a Down, itself, having denied being at the origin. American radio show guests “Lovelines” in 2002, Shavo Odadjian and John Dolmayan, respectively bassist and drummer of the group, said thus:
The song « Legend of Zelda » found on Morpheus, KaZaa or any other of these download platforms is not ours. (…) It was probably a kid in his room, with one of these new computer programs, who made this track and put it out claiming that it was System of a Down.
The nu metal band is far from the only one to have been wrongly attributed songs. In videos accumulating millions of views on YouTube, Bob Marley is still regularly rewarded with the interpretation of Don’t Worry Be Happy, Red, Red Wine or bad boys (songs by Bobby McFerrin, UB40 and Inner Circle); many punk tracks are connected to the Californians of Blink 182 (much to the chagrin of Lit and Me First and the Gimme Gimmes), and Nirvana has, in fact, never recorded a track titled Half the Man I Used to Be (it’s actually creepy, of Stone Temple Pilots).
The culprits of these unfounded beliefs? They are called eMule, Limewire, Kazaa or eDonkey. As the response made on the radio by members of System of a Down suggests, these pieces, which are still sometimes misattributed today, on the Web and in memories, are the direct result of the era of peer to peer (P2P, « peer to peer »direct exchanges between Internet users) and the birth of online piracy.
The scourge of an era
We are then in 2001. First P2P platform devoted to music, Napster has just closed its doors after two brief years of existence, under pressure from rights holders. Very quickly, other services followed: Kazaa, Limewire and especially eMule (previously called eDonkey2000)…, each has its own protocol, but all have a major difference compared to Napster: their decentralization.
“Because there was very little moderation, these fake files kept circulating”explains Ernesto Van Der Sar, of TorrentFreak
pornographic film instead of Matrixpirated version of Windows crippled with viruses, badly encoded Radiohead pieces… This decentralization is the main reason why, at the time, users quickly assimilated the idea that the file they are trying to hack might be poor quality, if at all what they were looking for. “In the late 1990s and early 2000s, the majority of sharing was done by average Internet users and it was more difficult to distinguish between quality content and poorly named files. And because there was very little moderation, these fake files kept circulating”explains Ernesto Van Der Sar, founder of the site TorrentFreak, specializing in issues of sharing, piracy and copyright.

The exchanges taking place between users, without going through a single database, the quality of a file and the associated information depended entirely on the goodwill of the person who made it available to the community. Not to mention that, at the time, 56K modems often forced users to wait several hours to download a file (thus multiplying the probability of making errors) and that the ratings and comments systems, which can help to separate the wheat from the chaff, were still very rare.
But why make available files that we know are not the right ones? « I think some people thought it would be ‘fun’ to bother downloaders with fake files », says Ernesto Van Der Sar. And, in fact, many American Internet users, today on the forums, remember that one of the recurring jokes of the time consisted in putting a declaration of Bill Clinton made at the time of the Monica Lewinsky affair in place and places most wanted files.
Added to this were the ill-intentioned people disguising malware under popular file names, and the others, more opportunistic, who renamed their files to correspond to the terms most searched for by Internet users. This guaranteed them to see them downloaded en masse and in turn allowed them to improve their “ratio” on sharing platforms, i.e. the ratio between what they download and what they make available. Important data, a bad ratio that can be accompanied by a slowdown in downloads, or even a ban. Some went even further in shenanigans, surfing on trends to make themselves known or to trick users. Like the American rapper Soulja Boy, who took off his career by making his songs look popular on download platforms.

Professionalization of hacking
This scourge of erroneous or corrupt files, denounced by the Federal Trade Commission, the American trade regulator, among others, has disappeared as practices have evolved and spread. “It was the BitTorrent protocol that took illegal downloading to an industrial scale”, explains Sylvain Dejean, lecturer at the University of La Rochelle and specialist in the digital economy and the Internet. According to the researcher, the joint arrival of broadband and new exchange technologies, such as BitTorrent, have gradually led to a « Community downloading ».
BitTorrent, born in 2001, has brought out closed groups, often based on cooptation
While services like eMule or Kazaa were completely open, BitTorrent, born in 2001, brought out closed groups, often based on cooptation. In these smaller communities, few bad files in circulation, according to the economist, since they were built on a « quality requirement » and with “a strictly controlled upload/download ratio”. Like Oink’s Pink Palace, whose origins writer Stephen Witt recounts in his book Assaulting the record empire: when a whole generation commits the same crime (Castor Astral, 2016), and who thus writes on the site of the Guardian : “While some files did indeed remain artifacts of unknown origins, originating from nondescript Internet dwellers, the vast majority of MP3s actually originated from a handful of organized groups. »
Added to this is a form of « professionalization » piracy, according to Ernesto Van Der Sar, linked to the structuring of the piracy economy and competition between platforms:
Twenty years ago, it was above all about sharing and discovering content. Today, people just want free music, and pirate sites exist to make money. If a site or service offers poor quality content, people will go to competitors.

If piracy still exists, it has radically changed its face: torrent files and direct downloading have given way to streaming, which today represents 95% of illegal content online, according to a report by Musso. And it is more books, sports competitions and series that are targeted today, due in particular to the proliferation of exclusive video content on platforms such as Netflix, Amazon Prime, Apple TV or Disney +: users who cannot pay for multiple subscriptions without hurting their bank account, they turn more to illegally uploaded content.
In the end, thanks to the appearance of comments, to various forums and a handful of articles, justice was finally done for System of a Down, but especially for the group which, for all these years, has unjustly despoiled The Legend of Zelda. Contrary to what Odadjian and Dolmayan suggested twenty years ago, the track was not recorded by a child playing on his computer but by a very real group: The Rabbit Joint, originally from Maryland. Composed of Joe Pleiman and Jesse Spence, we can still find the trace of the title thanks to another vestige of the Internet: MySpace.
Corrigendum on May 13 at 9:20 a.m.: fixed an error concerning the instrument played by Shavo Odadjian.